# Pomerium using Helm
This quick-start will show you how to deploy Pomerium with Helm (opens new window) on Kubernetes (opens new window).
# Prerequisites
- A Google Cloud Account (opens new window)
- A configured identity provider
- Install kubectl (opens new window)
- Install the Google Cloud SDK (opens new window)
- Install helm (opens new window)
- TLS certificates
Though there are many ways (opens new window) to work with Kubernetes, for the purpose of this guide, we will be using Google's Kubernetes Engine (opens new window). That said, most of the following steps should be very similar using any other provider.
In addition to sharing many of the same features as the Kubernetes quickstart guide, the default helm deployment script also includes a bootstrapped certificate authority enabling mutually authenticated and encrypted communication between services that does not depend on the external LetsEncrypt certificates. Having the external domain certificate de-coupled makes it easier to renew external certificates.
# Configure
Download and modify the following helm_gke.sh script and values file to match your identity provider and TLS certificates settings.
#!/bin/bash
# PRE-REQ: Install Helm : You should verify the content of this script before running.
# curl https://raw.githubusercontent.com/kubernetes/helm/master/scripts/get | bash
# NOTE! This will create real resources on Google's cloud. Make sure you clean up any unused
# resources to avoid being billed. For reference, this tutorial cost me <10 cents for a couple of hours.
# NOTE! You must change the identity provider client secret setting, and service account setting!
# NOTE! If you are using gsuite, you should also set `authenticate.idp.serviceAccount`, see docs !
echo "=> [GCE] creating cluster"
gcloud container clusters create pomerium --region us-west2 --num-nodes 1
echo "=> [GCE] get cluster credentials so we can use kubctl locally"
gcloud container clusters get-credentials pomerium --region us-west2
echo "=> add pomerium's helm repo"
helm repo add pomerium https://helm.pomerium.io
echo "=> update helm"
helm repo update
echo "=> add bitnami's helm repo"
helm repo add bitnami https://charts.bitnami.com/bitnami
echo "=> install nginx as a sample hello world app"
helm upgrade --install nginx bitnami/nginx --set service.type=ClusterIP
echo "=> install pomerium with helm"
helm install \
pomerium \
pomerium/pomerium \
--set service.type="NodePort" \
--set config.sharedSecret=$(head -c32 /dev/urandom | base64) \
--set config.cookieSecret=$(head -c32 /dev/urandom | base64) \
--set ingress.secret.name="pomerium-tls" \
--set ingress.secret.cert=$(base64 -i "$HOME/.acme.sh/*.corp.beyondperimeter.com_ecc/fullchain.cer") \
--set ingress.secret.key=$(base64 -i "$HOME/.acme.sh/*.corp.beyondperimeter.com_ecc/*.corp.beyondperimeter.com.key") \
--values docs/configuration/examples/kubernetes/values.yaml
# When done, clean up by deleting the cluster!
# helm del $(helm ls --all --short) --purge # deletes all your helm instances
# gcloud container clusters delete pomerium # deletes your cluster
authenticate:
idp:
provider: "google"
clientID: YOUR_CLIENT_ID
clientSecret: YOUR_SECRET
# Required for group data
# https://www.pomerium.com/configuration/#identity-provider-service-account
serviceAccount: YOUR_SERVICE_ACCOUNT
service:
annotations:
cloud.google.com/app-protocols: '{"https":"HTTPS"}'
proxy:
service:
annotations:
cloud.google.com/app-protocols: '{"https":"HTTPS"}'
service:
type: NodePort
config:
policy:
- from: https://hello.localhost.pomerium.io
to: http://nginx.default.svc.cluster.local:80
allowed_domains:
- gmail.com
ingress:
annotations:
kubernetes.io/ingress.allow-http: "false"
# Run
Run ./scripts/helm_gke.sh (opens new window) which will:
- Provision a new cluster.
- Create authenticate, authorize, and proxy deployments (opens new window).
- Provision and apply authenticate, authorize, and proxy services (opens new window).
- Configure an ingress, Google's default load balancer.
./scripts/helm_gke.sh
# Navigate
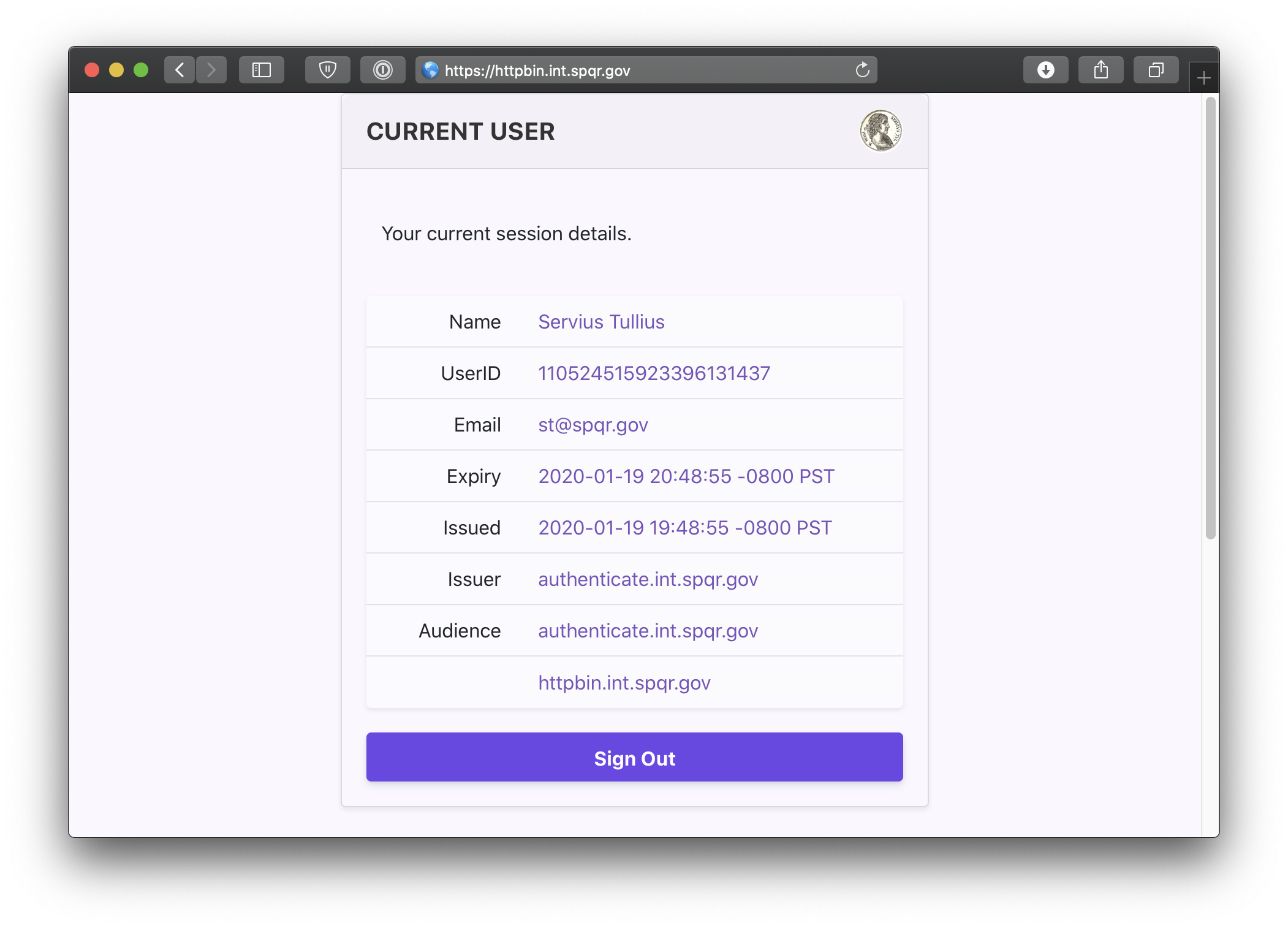
Open a browser and navigate to verify.your.domain.example.
You can also navigate to the special pomerium endpoint verify.your.domain.example/.pomerium/ to see your current user details.